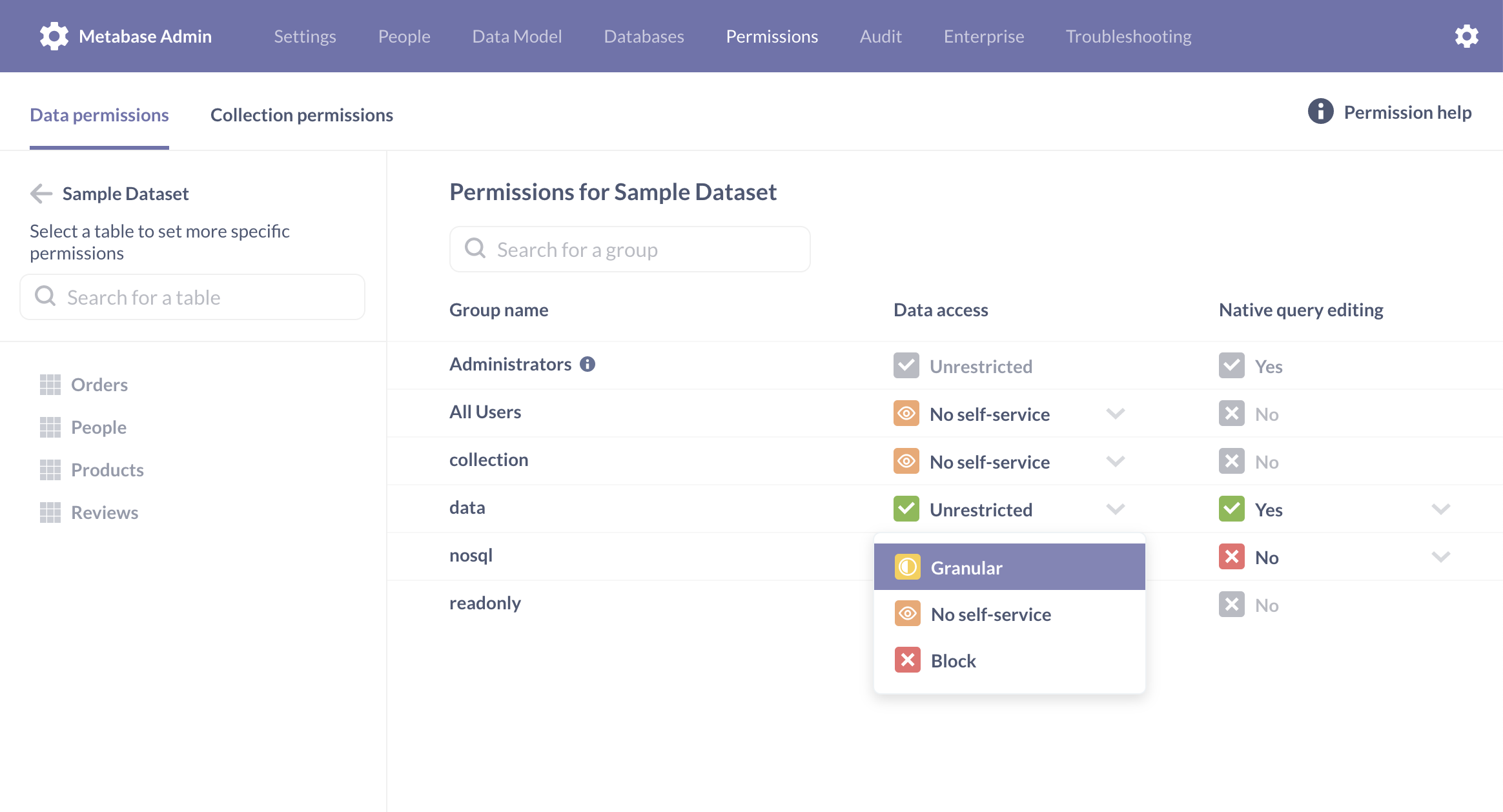
docs - general permissions (#21596)
Showing
- docs/README.md 1 addition, 0 deletionsdocs/README.md
- docs/administration-guide/05-setting-permissions.md 1 addition, 0 deletionsdocs/administration-guide/05-setting-permissions.md
- docs/administration-guide/data-permissions.md 33 additions, 16 deletionsdocs/administration-guide/data-permissions.md
- docs/administration-guide/general-permissions.md 26 additions, 0 deletionsdocs/administration-guide/general-permissions.md
- docs/administration-guide/images/permissions.png 0 additions, 0 deletionsdocs/administration-guide/images/permissions.png
- docs/administration-guide/start.md 3 additions, 1 deletiondocs/administration-guide/start.md
223 KiB